Supported identity providers
| Provider | Protocol | Status |
|---|---|---|
| Microsoft Azure AD (Entra ID) | OAuth 2.0 / OpenID Connect | Available |
| Okta | SAML / OIDC | Available on request |
| Google Workspace | OIDC | Available on request |
| Custom SAML/OIDC | SAML 2.0 / OIDC | Available on request |
For other identity providers, contact support@seal.run.
How SSO works
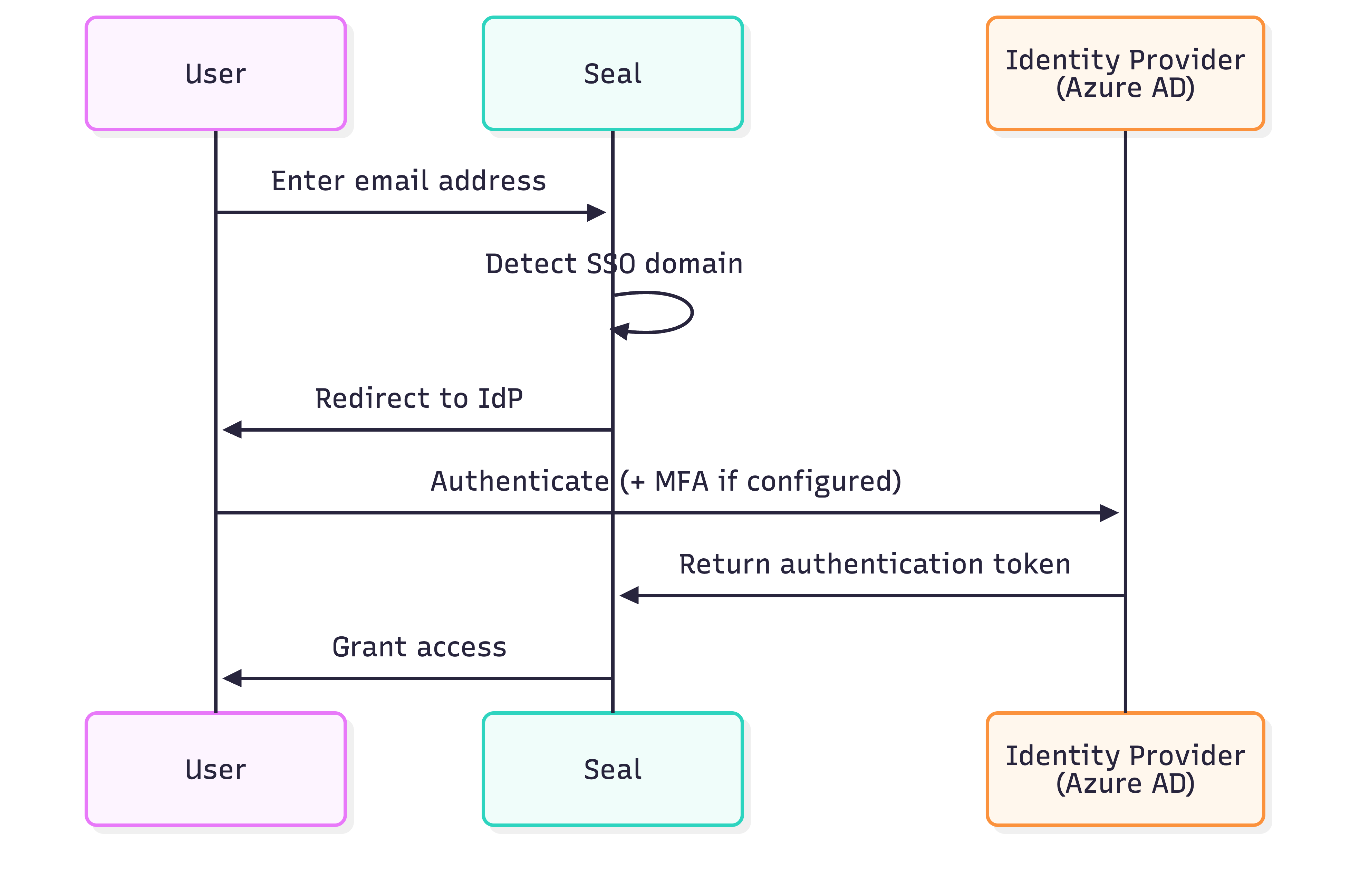
Domain-Based Routing
SSO is configured per organisation with specific email domains. Users with SSO-enabled domains are automatically redirected to the identity provider — password login is disabled for these domains.Configuration options
| Option | Description | Example |
|---|---|---|
| Identity Provider | SSO provider | Microsoft Azure AD |
| Email Domains | Domains requiring SSO | acme.com, acme.co.uk |
| Tenant ID | Organisation’s Azure AD tenant (optional) | xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx |
Security
| Feature | Details |
|---|---|
| Enforced SSO | Password login disabled for SSO domains |
| No password storage | Seal never receives or stores SSO user passwords |
| MFA inheritance | Users inherit MFA requirements from IdP |
| Session timeout | 15-minute inactivity timeout for Part 11 compliance (configurable). Applies to all authentication methods — SSO and native login. |
Setup
To enable SSO, provide:- Email domains for SSO enforcement
- Azure AD Tenant ID
- Technical contact
Contact support@seal.run to begin SSO setup.
Step-by-step guide for configuring SSO
Step-by-step guide for configuring SSO
Step 1: Find Your Azure Tenant ID
- Log in to the Azure Portal
- Go to Microsoft Azure → Manage Microsoft Entra ID
- On the Overview page, locate the Tenant ID field
- Copy the Tenant ID (it will be a GUID format like
12345678-1234-1234-1234-123456789abc)
Step 2: Create an OAuth 2.0 App Registration in Azure
- In the Azure Portal, use the search bar to navigate to App registrations
- Click New registration
- Fill in the registration details:
- Name:
Seal Platform SSO(or any descriptive name) - Supported account types: Select “Accounts in this organizational directory only” (single tenant)
- Redirect URI:
- Select Web as the platform type
- Your Seal contact will provide the redirect URI during setup
- Name:
- Click Register
Step 3: Provide Information to Seal
Send the following information to your Seal contact:- Azure Tenant ID (from Step 1)
- Email Domains (e.g.,
yourcompany.com, yourcompany.co.uk) - Technical contact
What Happens After You Provide the Information
Once Seal receives your information, we will configure SSO for your organization and notify you when it’s ready. This typically takes 1-2 business days.Testing SSO
After Seal completes the configuration:- Go to the Seal login page
- Enter an email address with one of your configured domains
- You should see a “Sign in with Microsoft” button
- Click the button and sign in with your Microsoft credentials
- You should be redirected back to Seal and logged in successfully
If you have an existing Seal account with a password, you may need to link your accounts on first SSO login. The system will guide you through this process.
User provisioning
| Method | Description |
|---|---|
| Just-in-Time (JIT) | Users auto-created on first SSO login |
| Manual | Admins pre-create accounts |
| SCIM | Automated provisioning/deprovisioning from IdP (enterprise) |